Exploring Crypto - Introduction to Blockchain
I'm excited to begin my journey into the crypto space with Minke, a decentralised finance wallet built on the Polygon network. Minke's mission is to democratise decentralised finance. This is the first in a series of articles exploring crypto leading up to a profile on Minke.
Current systems rely on powerful centralised parties and are susceptible to higher costs and other abuses. A key benefit of blockchain technology is its ability to create applications where trust can be decentralised away from these parties.
This article will explore blockchain computing, how it removes the need for powerful centralised parties and innovations that can improve the user experience and drive adoption. There will be a focus on areas relevant to Minke, such as Ethereum and Polygon.
The following article in this series will explore business model defensibility along with brief overviews of decentralised finance and Aave.
I hope that sharing my exploration of the space will help more people learn about crypto as we journey into this fascinating space together.
Index
Blockchain Computing
Decentralising Trust
Consensus Mechanisms and the Scalability Trilemma
Scaling Solutions and Polygon
Blockchain Computing
Segment Key Points
Current systems rely on centralised authorities, leading to costs such as higher fees and loan interest rates and lower deposit rates.
Blockchain technology removes the need to trust these centralised parties by replacing them with a combination of cryptography and incentives.
Creating applications where trust can be decentralised away from powerful central parties (e.g. Facebook/Meta) is the key benefit of blockchain technology.
A blockchain is a digital ledger or database record of transactions that is duplicated and distributed across a network of computers. Blockchain technology was made famous by the pseudonymous Satoshi Nakamoto in his Bitcoin white paper.
Satoshi Nakamoto’s Bitcoin white paper
We currently trust centralised authorities such as banks, governments and other institutions. This can lead to them monopolising power, resulting in higher costs and abuses.
Satoshi talks of the high costs of online commerce due to the reliance on financial institutions to act as trusted 3rd parties in transactions. These costs include fees, higher loan interest rates and lower deposit rates.
Blockchain technology addresses the issues of trust and centralisation. Satoshi believed these 3rd parties could be replaced with cryptography and incentives.
This makes the blockchain:
Trustless: There is no need for trusted 3rd parties or participants to trust each other. This is due to the transparency from copies of the transaction record being stored by various participants (distributed ledger) and incentives for participants to act in the network's best interests.
Immutable: Transactions are almost impossible to be tampered with or reversed.
The design of this digital system, including rules such as limiting the supply of Bitcoins to 21 million coins and the level of incentives, are programmed into Bitcoin’s source code.
The idea of blockchain computing was taken to another level in 2015 when Vitalik Buterin and his co-founders launched Ethereum.
Ethereum’s programming language allows developers to use the blockchain to go beyond cryptocurrency transactions to processing smart contracts.
A smart contract uses computer code on the blockchain to enforce agreements between parties rather than the courts in a typical legal contract.
Smart contracts are the building blocks for entire applications called decentralised applications or dapps.
The main difference to standard applications is that backend systems such as databases and user data are distributed across participating computers in the blockchain. I.e. there is no central authority or company (e.g. Facebook/Meta) controlling the application or user data.
Creating applications where trust can be decentralised away from powerful central parties is the key benefit of blockchain technology. The following section will discuss the cryptography and incentive structures that make this decentralisation possible.
Decentralising Trust
Segment Key Points
Satoshi's blockchain uses a combination of hash functions, public key cryptography and game theory to accurately record transactions without centralised authorities.
Blockchain miners contribute computing power as 'Proof of Work' to validate transactions in exchange for rewards like newly minted Bitcoins and transaction fees.
The set of rules agreed upon by decentralised participants is called the blockchain's consensus mechanism.
A general understanding of how blockchains decentralise trust will involve the following concepts:
Hash Functions
Digital Signatures – Public and Private Keys
Game Theory and Incentives
These concepts build on one another. I’ll explore each of these concepts before putting them together to explain the blockchain.
Hash Functions
Broadly, a hash function is a cryptographic algorithm that assigns a distinctive value to digital data. The hash output will always be a fixed length regardless of the size of the input. The example below uses the SHA-256 algorithm used in the Bitcoin blockchain’s Proof of Work.

Notice how different the hash outputs are despite the similar inputs Hello World and HelloWorld. This property of hash functions allows them to be used to ensure that the data hasn’t been tampered with.
To illustrate this, consider sending an email from Person A to Person B:
Step 1: Person A uses a SHA-256 hash function on her/his original email message. This will give a unique hash output.
Step 2: Person A sends both the email and unique hash output to Person B.
Step 3: Person B uses a SHA-256 function on the email she/he receives
Step 4: Person B compares this hash output with the hash output Person A sent. If both hash outputs match, Person B will know the email message hasn’t been tampered with.
Digital Signatures – Public and Private Keys
A public key is a cryptographic code (a string of numbers) that allows a person to receive cryptographic transactions. A corresponding private key is needed to ‘unlock’ this transaction and prove that the person is the owner of the public key address.

These keys are part of the public key cryptography framework, which incorporates ‘trap door’ functions. These are one-way mathematical functions that are easy to solve in one way but very difficult to solve in reverse.
This means that it is easy to solve/verify that the public key was generated from a particular private key. However, it is impossible to derive the private key from the public key itself.
Therefore, a person’s public key is analogous to her/his ‘bank account’ number that exists as an address on the blockchain. The private key corresponds to the password or digital signature needed to access this bank account.
When a person makes a transaction, she/he addresses it to the recipient’s public key address and signs the transaction with her/his private key.
Given the focus on decentralisation, a person’s private key is critical to proving ownership of the account and must be kept secret.
Game Theory and Incentives
Game theory is a study in interactive decision making where the outcome of each player depends on the actions of all the other players in the game. I.e. a player must consider the actions or choices of other players on deciding her/his strategy.
Satoshi’s solution solved a longstanding problem in computer science called the Byzantine Generals Problem. This focused on the issues faced by distributed systems when the information from various components in the system cannot be trusted due to malfunction etc.
The authors of the paper described a situation where a group of Byzantine generals needed to coordinate their attack on a city but couldn’t trust other generals or their lieutenants. To be successful, the generals need to form a consensus on rules of what constitutes a valid message.
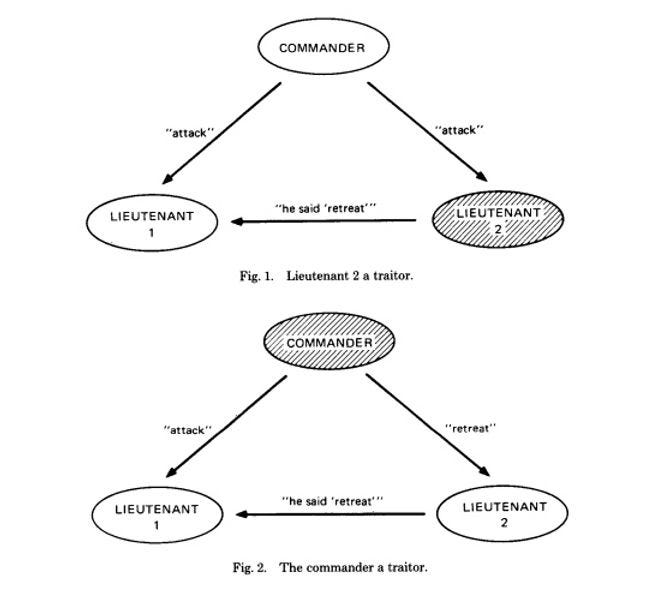
Satoshi’s blockchain solves this with:
Hash functions that prevent the message from being tampered with.
Public and Private key pairs that authenticate the sender of the message.
Authenticated messages are recorded and replicated across all participants. A false message from a participant will stand out and be ignored as long as the majority of the network is honest.
The above is combined with an incentive structure designed to keep participants honest. Blockchain ‘miners‘ are incentivised by rewards and fees such that it is more profitable to play by the rules. I.e. their best interests are aligned with that of the network.
The mining process will bring all these concepts together
Blockchain Mining
Blockchain miners run mining software that enables their computers to mine cryptocurrency (e.g. bitcoins) by adding new blocks to the blockchain.
The following will explain mining and how Satoshi’s blockchain operates.
Users sign transactions with their private keys, which go into a memory pool.
Miners on the blockchain network form a block by selecting a group of transactions from the memory pool. Before including the transactions, the miner checks the blockchain’s history to ensure the transaction is valid. E.g. checking the blockchain’s history to ensure that the sender of Bitcoin has the funds for the transaction.
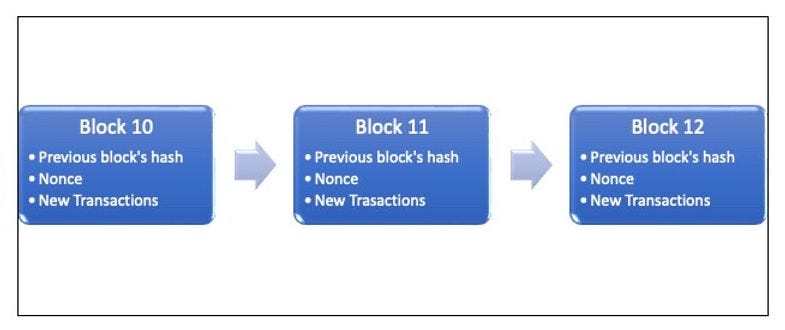
To simplify, each block contains the following key items:
A cryptographic hash of the previous block: This incorporates each block's history of previous transactions.
Nonce: Short form for ‘number only used once’. This is a number added to the bock by the miners to meet difficulty level requirements (explained further below).
New Transactions: Verified transactions selected by the miner to include in the block.
To mine or validate a block, miners use computing power to solve a mathematical problem. The blockchain network sets the mathematical level of difficulty according to the average time it takes to mine a block (10min per block in Bitcoin’s case).
The miner uses computing power to continually rehash a block to obtain a hash output that meets the threshold set by the blockchain network.
This is a process of trial and error where the miner keeps changing the nonce value until she/he finds a hash output that meets the threshold. The nonce allows the miner to obtain different hash values without changing the verified transactions or other details in the block.
Miners compete to be the first to mine a valid block and their success rate is proportional to the computing power they contribute to the blockchain. Bitcoin rewards these miners with a combination of newly minted Bitcoins (6.25 Bitcoins per block) and transaction fees.
The successfully validated block is added by thousands of participants to their copy of the blockchain (distributed ledger).
These blocks are linked in a chronological chain. The inclusion of the hash of previous blocks means that tampering with any block or transaction can easily be detected by other blockchain participants and will be rejected. i.e. the blockchain is immutable.
A malicious actor will need to acquire 51% of the network's computing power to force the network to accept transaction history changes. On a blockchain as large as Bitcoin, the cost will be excessive.
Additionally, any such actor will likely make more profit from following the rules as a breach will seriously impact the value of Bitcoins reducing whatever the actor hoped to gain by stealing.
The Ethereum blockchain’s mining process is largely similar with the following exceptions:
While Bitcoin’s focus is on becoming a medium of exchange or currency, Ethereum is aimed at creating smart contracts and applications.
These applications require ‘gas fees’ which are the required transaction fees to compensate miners for the computing energy required to run the various smart contracts.
Uses Ether or Eth as its cryptocurrency.
The above mining process allows trust to be decentralised and transactions or applications to be run without a central intermediary. Key to this is a set of rules or consensus mechanism that the network agrees to follow.
The above consensus mechanism is called ‘Proof of Work’. The following section will discuss these mechanisms and a framework to evaluate them.
Consensus Mechanisms and the Scalability Trilemma
Segment Key Points
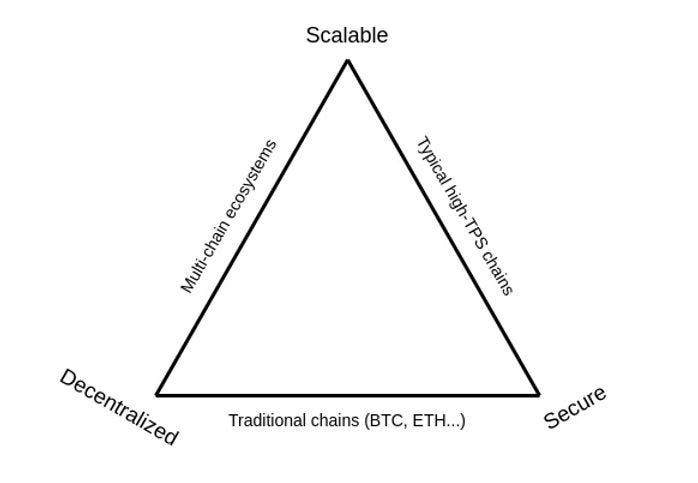
Blockchains currently need to make tradeoffs between decentralisation, security and scalability.
The Proof of Work consensus mechanism used by Bitcoin and Ethereum is decentralised and secure at the expense of scalability.
The numerous smart contracts built on Ethereum, such as defi apps and NFTs, are driving additional demand for solutions to improve scalability.
A blockchain network’s consensus mechanism is a set of rules for adding blocks to the blockchain that participants will agree to.
The Proof of Work consensus mechanism described previously is used by Bitcoin and Ethereum. These are the largest blockchains by market capitalisation (circa US$900 billion and US$405 billion, respectively).
This mechanism requires miners to use computing power to validate blocks. How do we evaluate the effectiveness of this consensus mechanism?
Ethereum co-founder Vitalik Buterin wrote about the ‘Scalability Trilemma’ faced by current blockchains.
He described the 3 properties of a blockchain as:
Decentralised: A decentralised network eliminates the need for a centralised intermediary. It also crowdsources consensus, i.e. no one party can control or censor the network.
Secure: Security reflects the lack of bugs and the difficulty of a party to gain control of the network
Scalable: Scalability refers to the blockchain’s ability to support high transaction throughput and, therefore, future growth/increased adoption.
Current blockchains struggle to be strong in all 3 properties. For example, a highly decentralised consensus mechanism (i.e. lots of participants) tends to be more secure as it is harder for a malicious player to acquire a large part of the network. However, this impacts scalability as it takes longer for a distributed network to reach a consensus.
Scalability is a key issue for Proof of Work mechanisms used by Bitcoin and Ethereum, resulting in large energy requirements, waiting times and high transaction costs. It is a particular issue for Ethereum.
Ethereum can create smart contracts that represent digital assets called Ethereum tokens. The Ethereum community standardised the creation of certain types of tokens.
Popular standards include ERC 721 used for non-fungible tokens and ERC 20 for fungible tokens used by applications like Aave. Defi apps like Aave are a collection of smart contracts built on Ethereum. These tokens and smart contracts drive demand for Ether and transactions on the Ethereum Blockchain. The boom in NFTs and Defi caused congestion and increased transaction costs on the Ethereum blockchain.
Other blockchains such as Solana have been created with more scalable consensus mechanisms. Solana transactions have transaction fees of a fraction of a cent compared to a few dollars for Bitcoin and circa $20 for Ethereum.
However, Solana has had several outages, which indicates potential compromises in security.
Recognising the issue of scalability and transaction costs, Ethereum is undergoing an upgrade over 2022 and 2023.
In April-June this year, Ethereum will transition to a Proof of Stake consensus mechanism. Miners pledge a ‘stake’ of the cryptocurrency (in this case, Ether) to be eligible to validate transactions and earn rewards. These stakes add a layer of security as miners could lose their staked amounts if the blocks are incorrectly validated.
This approach is more scalable as a miner’s probability of success is related to the amount staked rather than computing power. However, there are limits to how scalable the Ethereum blockchain itself can be.
Scaling Solutions and Polygon
Segment Key Points
Polygon is the predominant Layer 2 scaling solution for Ethereum.
Polygon's association with Ethereum allows applications such as Aave to be brought over to the Polygon network and benefit from lower transaction costs and improved user experience.
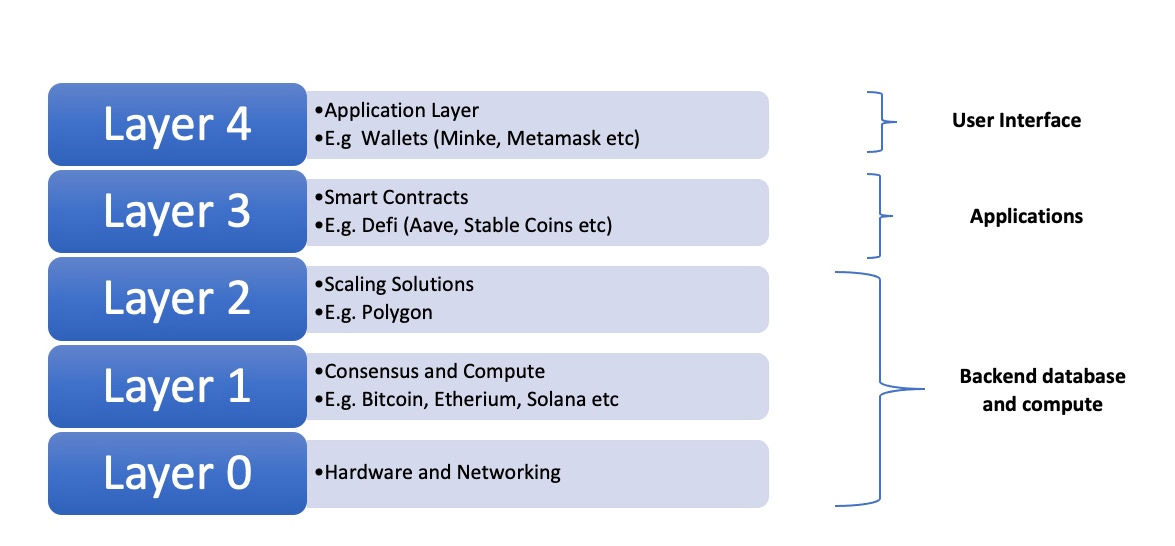
Ethereum, Polygon and defi apps like Aave represent different layers in a technology stack based on decentralisation of trust. This will be explored further in the next article.
A more scalable approach would be to ‘outsource’ some of the work to a new layer built on top of the main blockchain. For Ethereum, the predominant ‘Layer 2’ scaling solution is called Polygon.
Polygon uses Commit chains, which are transaction networks operating adjacent to the Ethereum Blockchain. These commit chains bundle batches of transactions, confirm them en masse and record this data on the Ethereum Blockchain.
The Commit chains use a Proof of Stake consensus mechanism to validate the blocks to be committed to the Ethereum blockchain.
Polygon has its own currency or tokens called Matic. This is used for staking as well as to run smart contracts.
An important feature of Polygon is that it allows existing Ethereum applications to be ported over easily. This includes decentralised finance applications (defi apps) such as borrowing and lending platform Aave that Minke will integrate with.
Albeit, Polygon is also subject to security risks as evidenced by a hack in late 2021. This will be explored further in subsequent posts.
So far, we’ve discussed blockchains (Bitcoin, Ethereum), scaling solutions (Polygon) and smart contract defi apps (Aave). Notice how these solutions seem to build on top of one another in layers.
The above is a popular framework used to categorise businesses being built in the crypto space and closely represents a computing stack.
In this way, blockchain technology can be seen as a computing paradigm built on the decentralisation of trust. A subsequent article will explore this further, along with business model defensibility and brief overviews of defi and Aave.